CYBER DEFENSE GAME CONCEPT
We live in a digital age where we have a wealth of knowledge
at our fingertips. The bounty of the internet lets us share,
explore, buy, create, and coordinate like never before. However,
digital perils also threaten us. Cyber attacks are launched every
minute against our citizenry.
The game Cyber Defense thematically explores concepts in cyber security.
Modern computer systems are vulnerable to cyber attacks, and there
needs to be a constant vigil to keep computer systems safe against cyber
intrusion through cyber security measures. Common types of cyber
attacks include Phishing, Man-in-the-middle and Distributed Denial
of Service (DDOS) attacks. In Cyber Defense, one player plays as
the Hacker, and the other player plays as the Defender.
AREA CONTROL GENRE -
Cyber Defense is an Area Control Genre Game.
In this genre of games, players vie for spaces or areas through
attacks, strength or presence. Players use resources or forces that
can be mustered into an area to try to gain dominance in the zone.
Often, multiple players can occupy the same space, and controlling
an area grants a player advantages and resources.
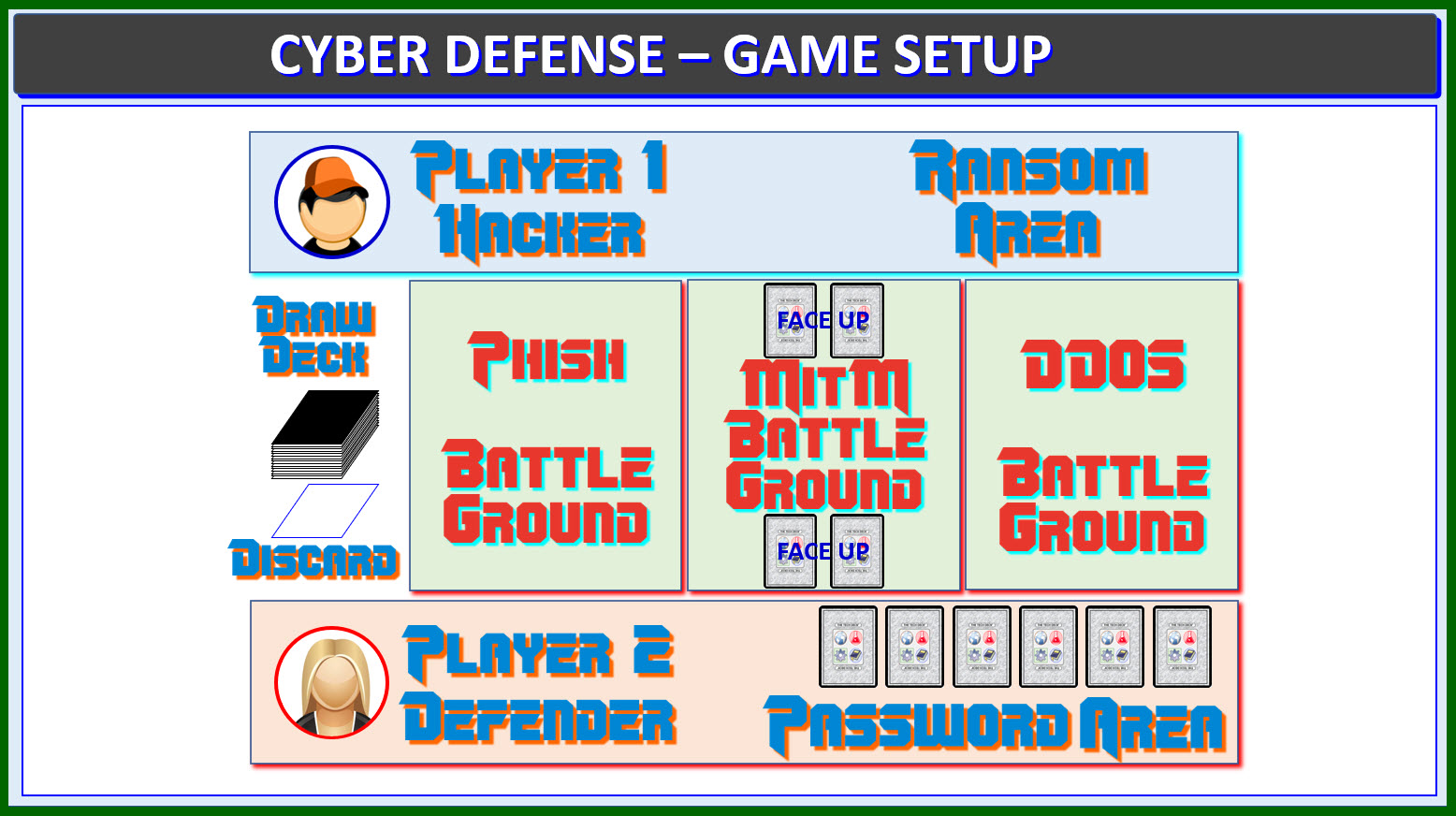
CYBER DEFENSE GAME SETUP
BATTLEGROUND AREAS -
There are 3 battlegrounds: Phishing, Man-in-the-middle and
DDOS battlegrounds. Mark these three regions in the play area
with face down cards, playing cards or blank paper.
DRAW DECK -
Expel the Wild Cards.
Shuffle the remaining cards to form a draw deck.
DISCARD PILES -
The deck has a discard pile next to it (that starts with
no cards in it).
DEAL CARDS -
Each Player is dealt 10 cards, drawn from the draw deck.
DETERMINE ROLES -
Roles are randomly determined. One player is the hacker
(starting player), one player is the defender.
PASSWORD -
Deal 6 face down cards in a row into the defender's
password area. The defender may look at these at anytime.
MITM CARDS -
Deal 2 cards face up for each player into the MitM Battleground.
CYBER DEFENSE GAME PLAY OVERVIEW
Cyber Defense is played over 3 rounds, each round
is composed of these steps:
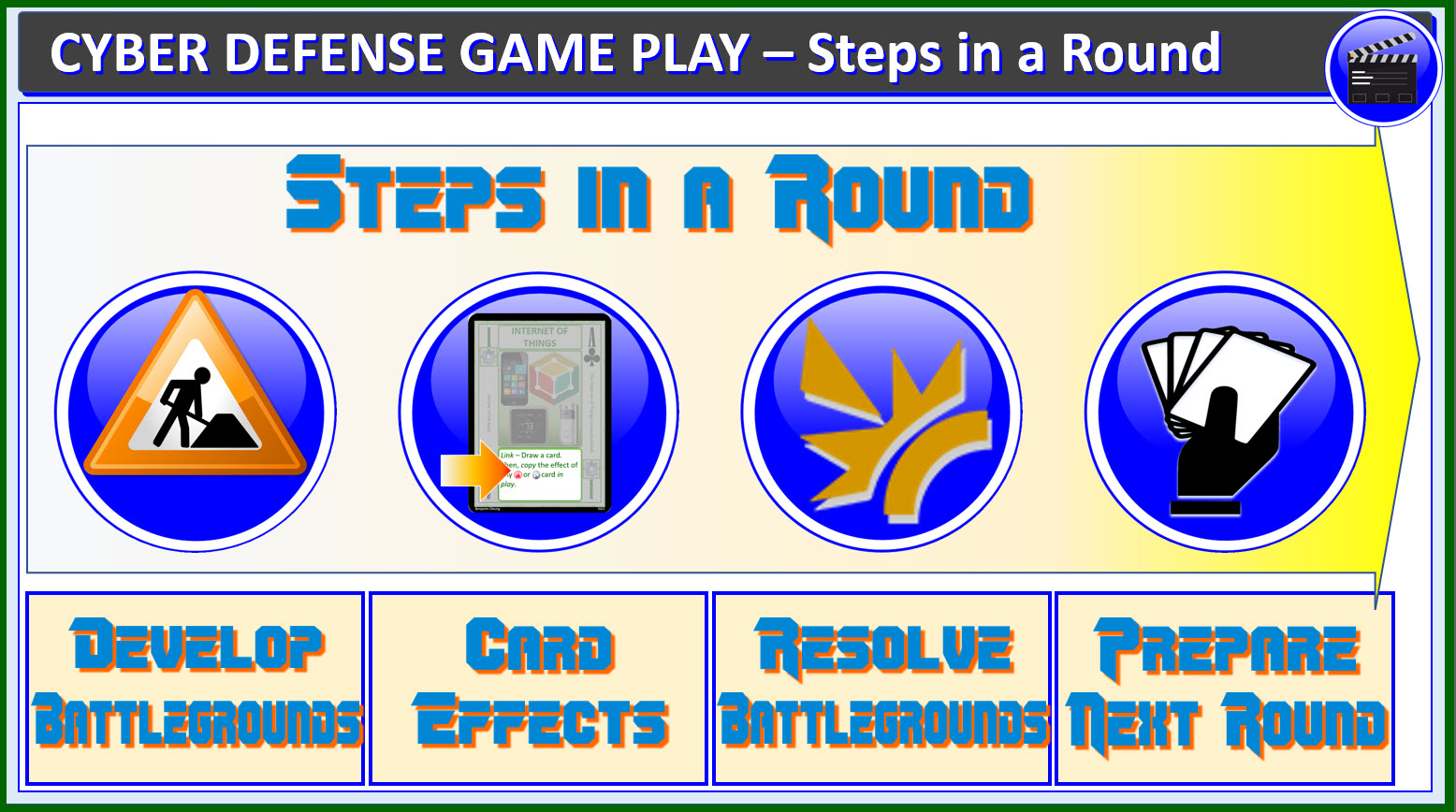
DEVELOP BATTLEGROUNDS
Players take turns playing cards into any of the three
Battlegrounds (BG) until each player has played 9 cards into
the three Battlegrounds. Cards played into the Phish and DDOS
Battlegrounds are played face down. MitM Battlegrounds cards
are played face up. Each BG must have one card played to it.
There is no maximum.

These are the rules regarding the Development of Battlegrounds
PLAY -
Players take turns playing cards into any of the three Battlegrounds until each player has played 9 cards into the three Battlegrounds.
PHISH & DDOS -
Cards played in the Phish and DDOS Battleground are played face down.
MITM BATTLEGROUND -
MitM Battlegrounds cards are played face up.
BG MINIMUM -
Every BG must have at least 1 card played to it. There is no maximum to the number of cards a BG can hold.
USE A CARD EFFECT
Players alternate using up to two Card Effects in their
Man-in-the-Middle (MitM) BG (see below).

These are the rules regarding the Playing Card Effects
GAME EFFECTS -
Players alternate using game effects from up to two different
Man-in-the-Middle cards that they control. The effects can be
applied to any of the Battlegrounds.
NEUTRAL CARDS -
All cards in any of the battlegrounds are owned by their respective
players. But they are also considered Neutral Cards for Tech Deck
game effects purposes. However, Password cards are not considered
in play for game effect purposes and may not be affected by game
effects.
DEVELOP BATTLEGROUND -
After using a Game Effect on a Card, you can play a card to
any Battleground.
SEARCH EFFECTS -
The Hacker may not use Game effects that search the deck
(9 of Knowledge, 6 and 11 of Technology). However, the Defender
may use cards that search the deck.
RESOLVING BATTLEGROUNDS
Each battleground is resolved starting with the Phish BG,
then the MitM BG and lastly the DDOS BG (see below).
These are the rules regarding the Resolving Battlegrounds.
Resolve each BG separately and sequentially.
PHISH BATTLEGROUND -
[Theme: Seeing Information] - The highest value card wins the Phish
BG. Use Tech Deck tie breaker rules (Knowledge [lowest suit]-
Science-Technology-Service [Highest suit]). If the Hacker wins,
they reveal one password digit card of the Defender. If possible,
first reveal a non-upgraded digit. Then, the Hacker makes 2
guesses. If the Defender wins, they can unlock a locked digit.
The Hacker makes 1 guess.
MITM BATTLEGROUND -
[Theme: eavesdrop insertion] - The highest total sum value of the
all the MitM cards wins the MitM BG. High card is the tie breaker.
If Hacker wins, they make 4 guesses (2 bonus guesses). If the
Defender wins, the Hacker makes no guesses.
DDOS BATTLEGROUND -
[Theme: Overwhelming Attack] - Arrange the DDOS cards from high to low
for each player. Compare each pair of Hacker & Defender cards from low
to high. The DDOS Winner is the one who wins the most comparisons. Each
opposing pair of lowest-value cards counts as one comparison win. If
one player has more cards in their DDOS BG than another it counts and
a 1:0 win for that comparisons. Use Tech Deck tie-breaker rules. If the
Hacker wins, they can lock one digit in the Defender's password
preventing it from being upgraded. Slide the card back to indicate it
is locked. The Hacker make 2 guesses. If the Defender wins, they can
upgrade a password digit. The Hacker makes 1 guess.
PASSWORD GUESSES
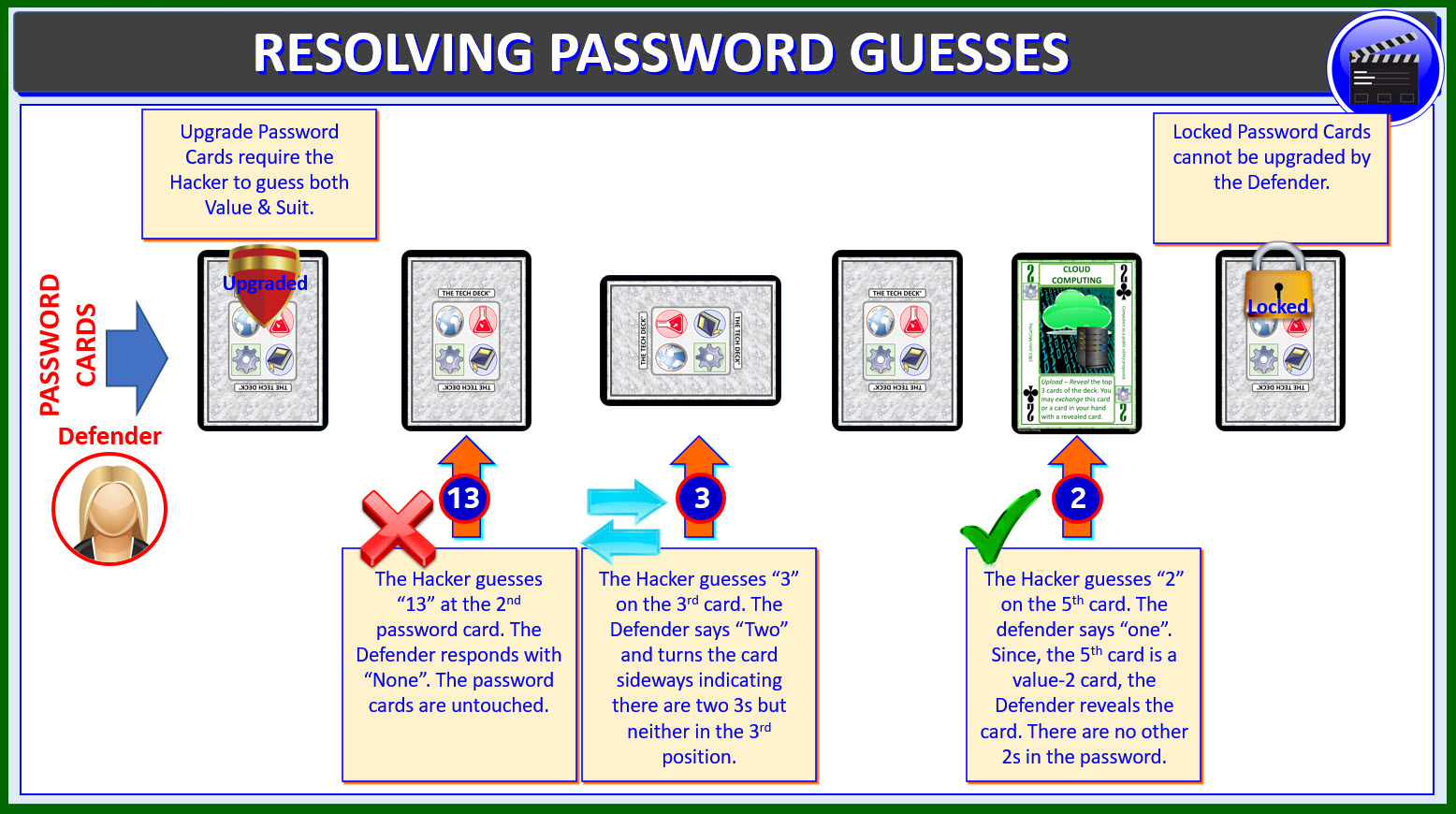
These are the rules for handling the Password Guesses
MAKING A GUESS -
The Hacker selects a card (position in the password) and makes a
guess, stating a number from 1 to 13. If he selects an upgraded
digit, he names both a value and suit instead.
MARKING A GUESS -
If the Hacker guesses a number that is in the password but not in that
position, the Defender states how many of that guessed number are in
the password and turns the target card sideways. This indicates that
the card is not of that value, but the value is in the password. If
the Hacker guesses the proper suit of an upgraded password digit but
not the right value, the card is turned upside down (180 degrees). If the
value is not in the password, the Defender says that there are no digits
of that value and leaves the selected card alone. The Defender's response
considers previously revealed digits. If the card is already turned
sideways, and it is selected as a card for a guess again, it is only
turned again only for a guess if it is an upgraded digit.
CORRECT GUESS -
If the Hacker selects a non-upgraded password card and it matches the
number, the Defender reveals that password digit. If the Hacker makes
a correct guess for an upgraded password digit with both number and
suit the Defender reveals that password digit.
PREPARE THE NEXT ROUND
Prepare the next round. Gather all cards (except password cards)
to form a new draw deck. Each player is dealt 10 cards. Deal 2
cards face up for each player into the MitM BG. The game ends
after 3 rounds. The first player alternates.

Players prepare the next round of play by:
CREATE A NEW DECK -
Take all cards (except for the password cards) together including
the cards used by the Hacker to guess the Defender's password to
create a new Draw deck for the next round.
DEAL CARDS -
Deal each Player 10 cards from the draw deck.
GAME END -
The game ends after 3 rounds.
FIRST PLAYER -
The first player alternates.
MITM CARDS -
Deal 2 cards face up for each player into the MitM Battleground.
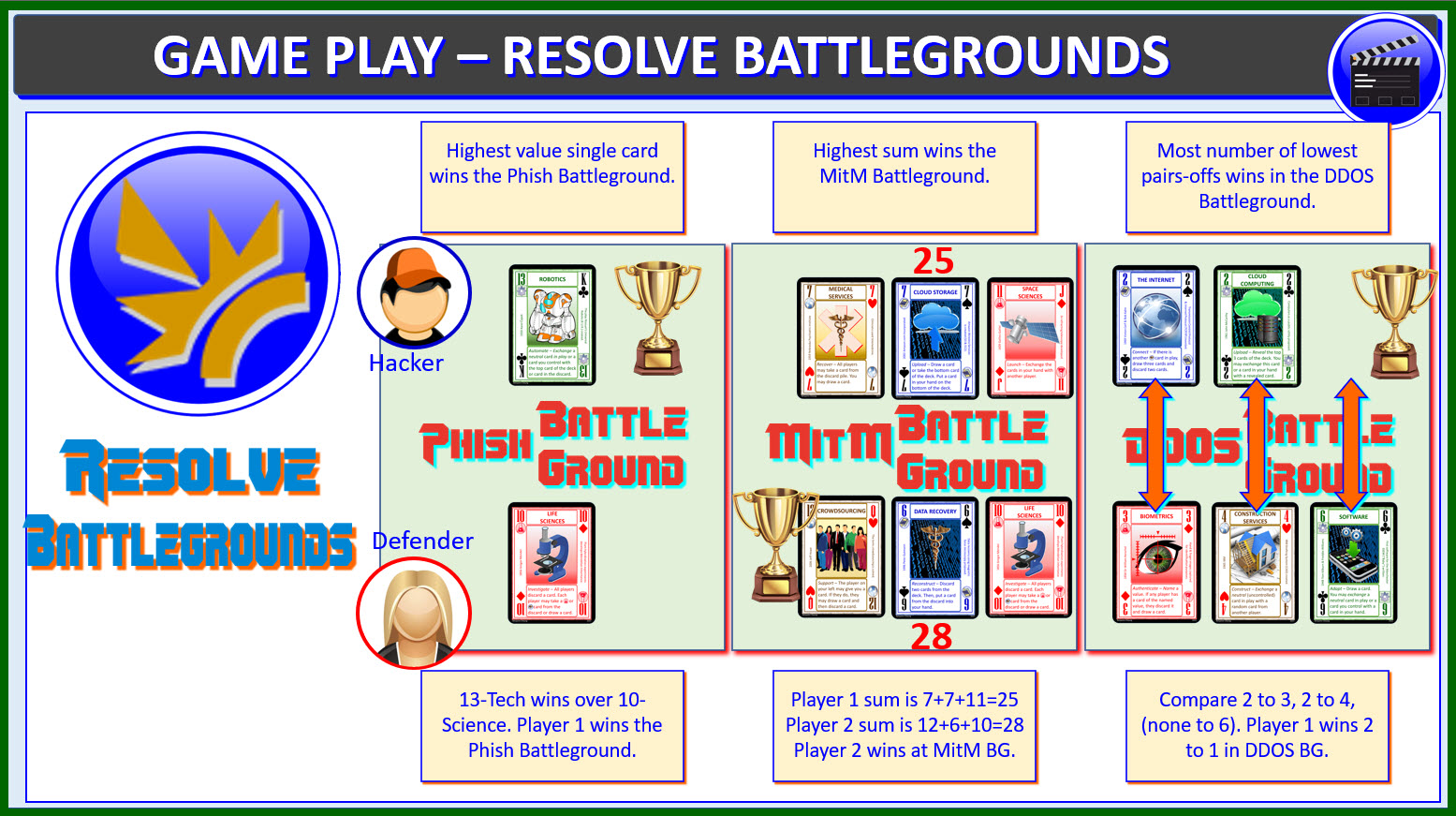
CYBER DEFENSE RESOLVING PHISH BATTLEGROUND EXAMPLE
Resolving Phish Battleground Example

The player with the highest value single card wins the Phish BG.
There are two examples in this diagram.
In Example #1:
Hacker wins with 13-Tech besting the Defender's 10-Science.
The Hacker wins and gets to reveal (turns over) a digit in the Defender's
password and he makes 2 guesses. The Defender played two cards into
the Phish BG, but only the highest card (10-Science) is considered.
In Example #2:
Here, the Defender wins the Phish BG because 12 Service wins over
the 7 Knowledge. The Defender wins and unlocks a digit in her
password and the Hacker makes only 1 guess.
CYBER DEFENSE RESOLVING MITM BATTLEGROUND EXAMPLE
Resolving MitM Battleground Example

The player with the highest total sum value of the all the MitM
cards wins the MitM BG. There are two examples here in the diagram.
In Example #1:
Here 25 > 16. So, the Hacker wins the comparison and as a result gets
to make 4 guesses (2 bonus guesses).
In Example #2:
In example 2, the Defender wins as 7+4+10 = (21) is greater than
13+2+2 = (17).
When the Defender wins, the Hacker makes no guesses.
CYBER DEFENSE RESOLVING DDOS BATTLEGROUND EXAMPLE
Resolving DDOS Battleground Example
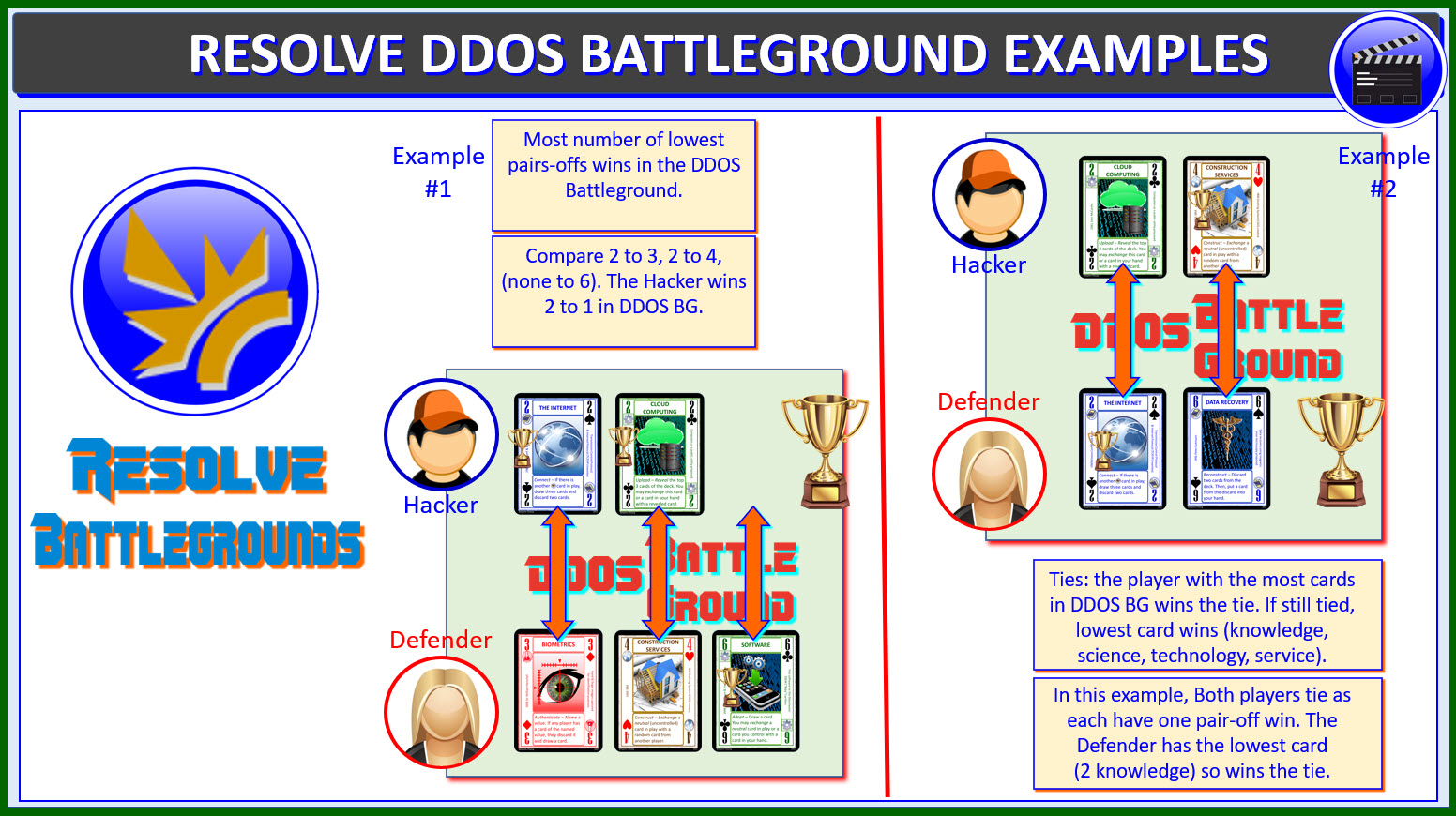
The player with the most number of lowest pairs-offs wins in the
DDOS Battleground. There are two examples in the diagram.
In Example #1:
Compare 2 to 3, 2 to 4, (none to 6). The Hacker wins 2 to 1 in DDOS BG.
In Example #2:
Ties: the player with the most cards in DDOS BG wins the tie. If
still tied, lowest card wins (knowledge, science, technology, service).
In this example, both players tie as each have one pair-off win. The
Defender has the lowest card (2 knowledge) so wins the tie.
DOWNLOAD THE RULES
Cyber Defense Full Rules:
Cyber Defense Rules Full
Cyber Defense Compact Rules:
Cyber Defense Rules Compact
CYBER DEFENSE INTRODUCTION VIDEO
Click below to watch a introduction video for Cyber Defense.
The introduction video describes the basic concepts,
objectives and an introduction to the Tech Deck.
CYBER DEFENSE PLAY GUIDE VIDEO
Watch a play guide video for Cyber Defense. The play guide
video is an in depth video on how to setup the game,
and all the steps involved in playing the game.
ENTRY ON BOARD GAME GEEK
You can read and explore the
BoardGameGeek entry for CYBER DEFENSE.
PUBLICATION INFORMATION
·
Published: April 1, 2024
·
Format: Card Game
·
Elements: 54 Cards
·
Size: 3.75" x 2.8751" x .875"
ORDERING CYBER DEFENSE
·
To purchase the Tech Deck:
Contact Me
EXPLORE OTHER TECH DECK GAMES